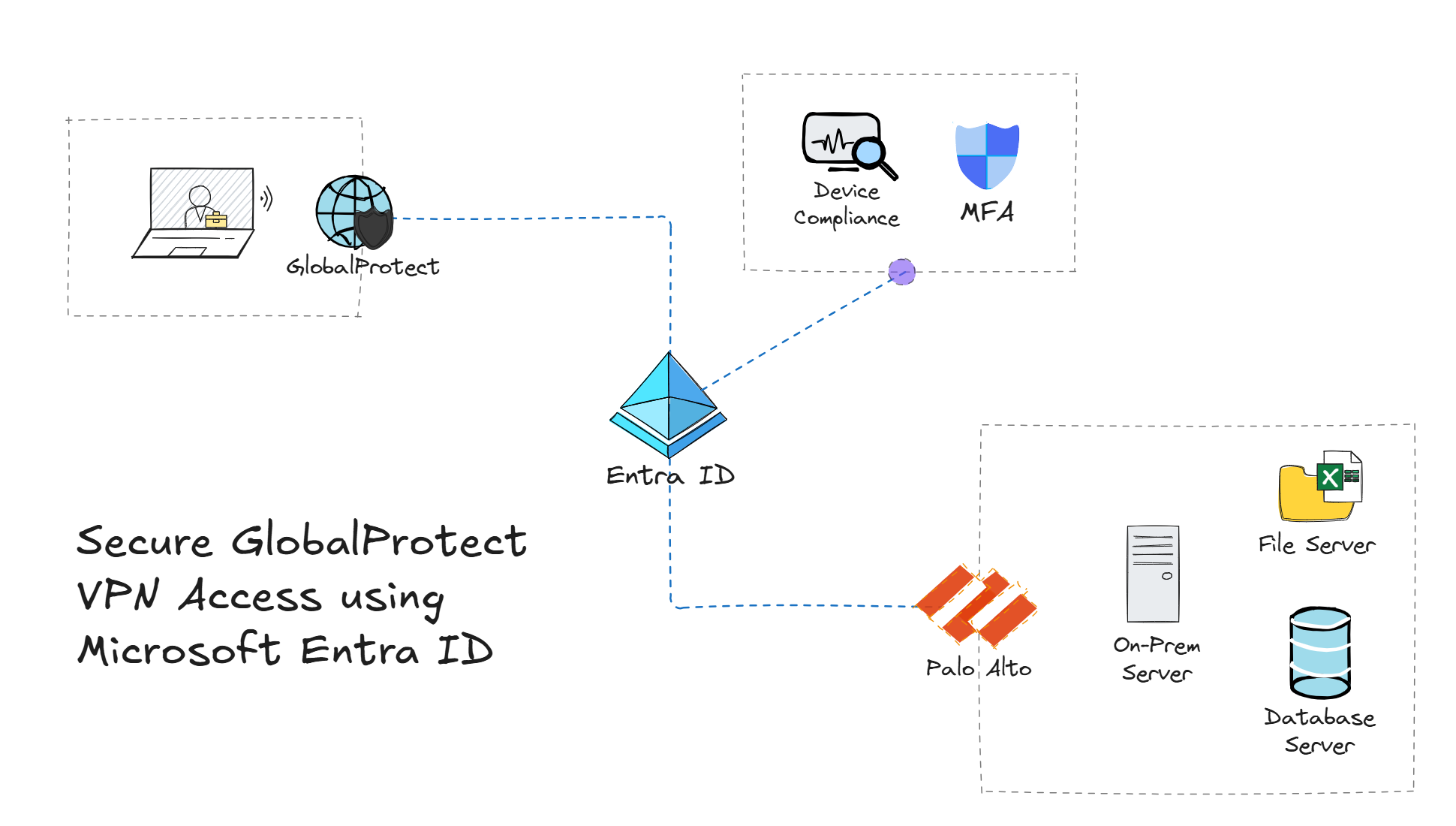
Traditional environments using Palo Alto GlobalProtect for VPN access have relied on using methods such as usernames and passwords, as well as certificates to authenticate users. However, in a Zero Trust world, it's important to verify explicitly, enforce least privilege, and assume breach. This is where Microsoft Entra ID comes in - enabling organizations to secure GlobalProtect with Single Sign-On (SSO) and Conditional Access (CA) policies.