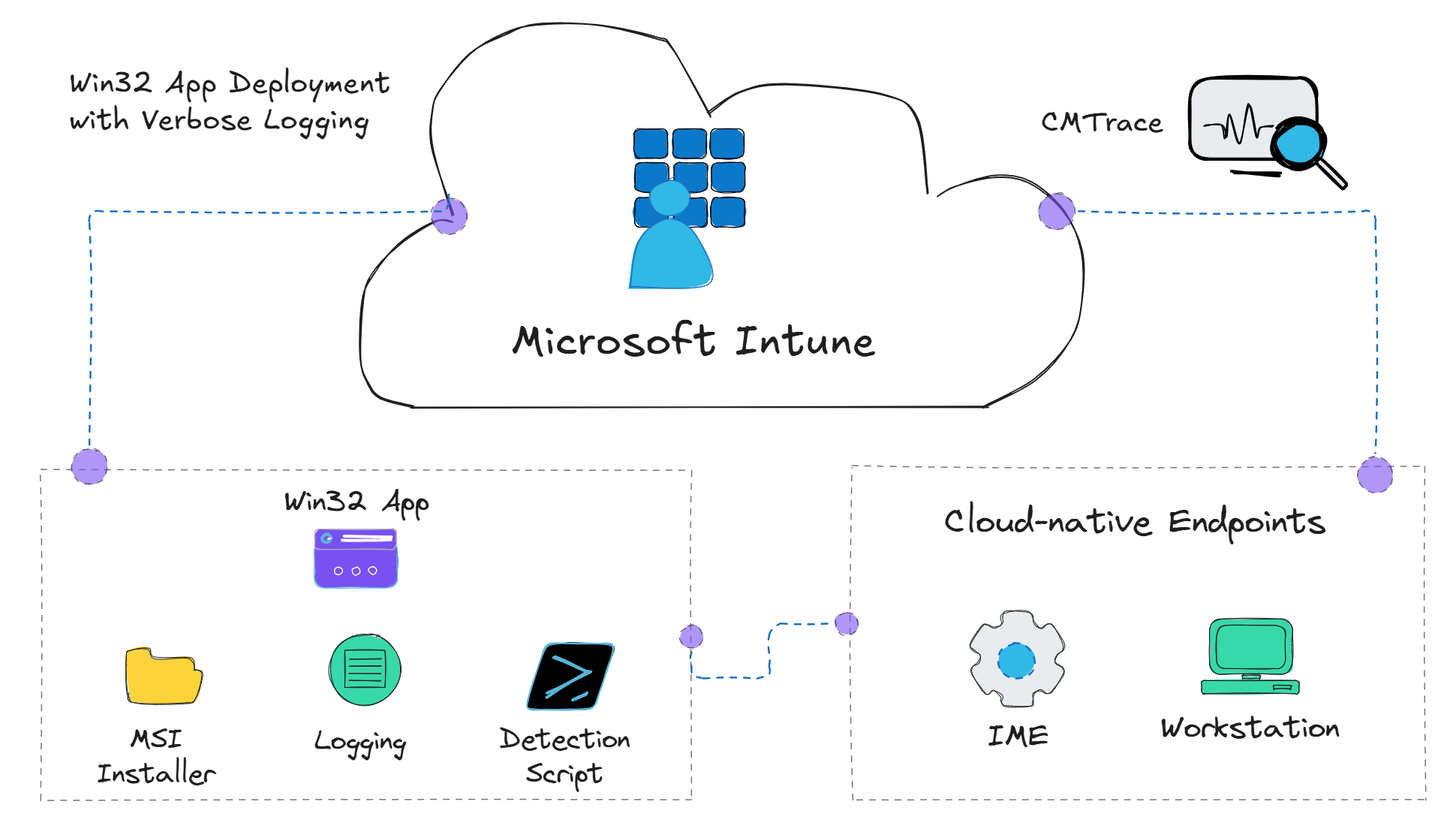
When deploying applications using Microsoft Intune, installing applications using the line-of-business (LOB) deployment method can make the process of deploying applications easier. However, once installations being deployed using LOB start failing, very little logging information is available to troubleshoot the issue. This is where Win32 app deployment shines 🤩
Overview
When deploying applications using Win32 app deployment, the installation process is handled by the Intune Management Extension (IME). The IME folder on a Windows client managed by Intune contains log files that can be used for troubleshooting issues — even better, these log files can be retrieved remotely from the Intune admin center. Furthermore, the IME folder can be used to add additional log files, such as verbose logging output from MSI installations. The logs are stored in the C:\ProgramData\Microsoft\IntuneManagementExtension\Logs folder on the client machine. This article explains how to create a Win32 app in Intune to install applications with verbose logging.
Log files from the following location on the client machine: C:\ProgramData\Microsoft\IntuneManagementExtension\Logs can be collected remotely by navigating to Intune admin portal > Devices > All devices > Select the device > Collect diagnostics > Yes.
This will collect the logs from the device and store them in a .zip file. To download the logs: from the selected device options, click Device diagnostics, click the ellipsis (...) and click Download. The logs will be downloaded to your local machine.
Prerequisites
- Microsoft Intune subscription
- Microsoft Win32 Content Prep Tool
- Windows 10 or later client machine
Step 1: Use the Microsoft Win32 Content Prep Tool to prepare the application for deployment
In this example, we will be using the BeyondTrust Remote Support agent as an example. The installation file is a .msi file.
- Download the Microsoft Win32 Content Prep Tool from the the tool's official Microsoft Github.
- Extract the contents of the downloaded file to a folder on your local machine.
- Create a folder on your local machine to store the application files. For example, create a folder called beyond-trust.
- For the sake of this example, we will copy the sra-pin-win_x64.msi (Beyond Trust agent installer) file and the IntuneWinAppUtil.exe to the beyond-trust folder.
- Once the files are copied, double click the IntuneWinAppUtil.exe file to begin the process of creating a
intunewin file.

Once the process completes, there should now be a sra-pin-win_x64.intunewin file in the beyond-trust folder created in a previous step. The .intunewin file will be used later when creating a Win32 app deployment.
Step 2: Create a Win32 app in Intune
Note: The initial configuration attempt is expected to fail due to the KEY_INFO= parameter not being set. This is expected behavior. The KEY_INFO= parameter with the appropriate key is required for the Beyond Trust agent installation to succeed. This will provide us an opportunity to review the logs and troubleshoot the installation error.
- Sign in to the Microsoft Intune admin portal.
- In the left navigation pane, select Apps > All apps > + Create.
- In the Select app type pane, select Windows app (Win32) and click Select.
- In the App information pane, select the App package file and click Select file.
- In the Select app package file pane, select the
sra-pin-win_x64.intunewin file created in a previous step and click OK.
- Fill out the following required fields:
- App information
- Program
- Requirements
- Detection rules
- Name: BeyondTrust Remote Support Agent
- Description: BeyondTrust Remote Support Agent
- Publisher: BeyondTrust
Store the verbose logging information in "%programdata%\Microsoft\IntuneManagementExtension\Logs\BeyondTrust.log" so the logs can be collected remotely from the Intune admin portal.
- Install command:
msiexec /i "sra-pin-win_x64.msi" ALLUSERS=1 /qn /norestart /l*v "%programdata%\Microsoft\IntuneManagementExtension\Logs\BeyondTrust.log"
- Uninstall command:
msiexec /x "{GUID}" /qn (replace {GUID} with the actual GUID of the application).
Intune should automatically add the GUID information pulled from the uploaded .intunewin file.
If it does not, you can find the GUID in the App information pane under App package file. The GUID is located in the sra-pin-win_x64.msi file name.
- Install behavior: System
- Device restart behavior: No specific action
- Operating system architecture: 64-bit
- Minimum operating system: Windows 10 1607
- Rule format: Use a custom detection script
- Script file: Upload a PowerShell detection script to check whether the application is installed.
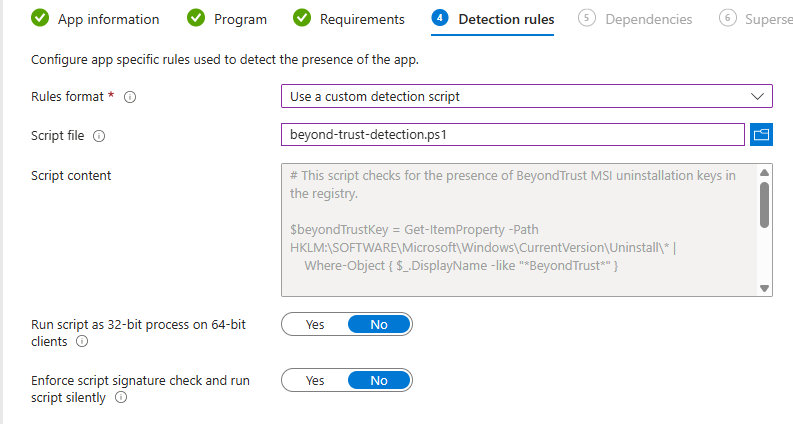
The following PowerShell script can be used to detect whether the BeyondTrust uninstall GUID is present in the MSI uninstall registry hivekey:
BeyondTrust Detection Script
Step 3: Troubleshoot the installation failure
As expected, the installation failed. Let's investigate 🔍 to find out why.

Oh no! We weren't able to install our remote support agent, so we'll have to go on-site 🚗 to troubleshoot the issue. Just kidding! 😁 Since we specified that the MSI verbose log file be created in the same directory as the IME log files, we can download the MSI verbose log file directly from the Intune admin portal.
- Navigate to Intune admin portal > Devices > All devices > Select the device > Collect diagnostics > Yes.
- Once the diagnostics retrieved from the endpoint is complete, from the selected device options, click Device diagnostics, click the ellipsis (...) and click Download.
- Extract the contents of the downloaded .zip file to a folder on your local machine.
- Open the C:\ProgramData\Microsoft\IntuneManagementExtension\Logs folder and locate the BeyondTrust.log file.
- Open the FoldersFiles ProgramData_Microsoft_IntuneManagementExtension_Logs folder and locate the BeyondTrust.log file.
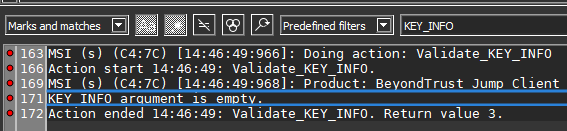
Open the BeyondTrust.log file in a text editor of your choice (e.g., CMTrace, Notepad, etc.). For this example, an open source log viewer called KLOG is being used. Search for the keyword KEY_INFO= in the BeyondTrust.log file to find the line that contains the error message. As expected, the installation failed because the KEY_INFO= parameter was not set. The error message will look something like the image below:
Step 4: Fix MSI install parameters and redeploy
Now that we know the installation failed because the KEY_INFO= parameter was not set, we can fix the install command and redeploy the application.
- Navigate to the Beyond Trust Win32 app in Intune and click Properties > Program > Edit.
- In the Install command field under the Program tab, add the
KEY_INFO= parameter with the appropriate key. The install command should look something like this:
msiexec /i "sra-pin-win_x64.msi" ALLUSERS=1 /qn /norestart /l*v "%programdata%\Microsoft\IntuneManagementExtension\Logs\BeyondTrust.log" KEY_INFO="randomkeyvalueprovdedbybeyondtrust"
- Click Review + save to continue through updating the Win32 app, and click Save to save the changes to the Win32 app.
Now, the next time the endpoint (IME) checks in with Intune, the application will be installed successfully.
If you need to manually force the IME to retry a failed Win32 app installation, take a look at this awesome blog post by Rudy Ooms going over multiple ways to force the IME to retry a failed Win32 app installation.
And there we have it! The application is now installed successfully. 🎉

Conclusion
Using the Win32 app deployment method in Intune provides verbose logging information that can be used to troubleshoot installation issues. This can make it easier to identify and fix issues with application installations. By following the steps outlined in this article, you can create a Win32 app in Intune to install applications with verbose logging.